Tales From the Underside: A Kremlin-Approved Hack, Leak & Doxxing Operation
23 August 2022
Note on links: Hyperlinks in this article go to archived sources and references, and are safe to click on. The briefing does not contain live links to the Underside site or documents. It is strongly recommended to take appropriate security measures if exploring the Underside or Britishfiles websites and documents directly, as it is possible that they may contain malware.
_________________________________________________________________________________
“Underside” is an extensive doxxing operation targeting alleged British-influenced traitors and infiltrators within Russia, including journalists, civil society activists, business people and even Russian politicians. It uses a website (underside[.]today) to publish long-form articles on individuals and organisations, which it also promotes via its Telegram channel. It draws on a combination of open source information and hacked documents primarily from British government and civil society organisations, particularly the Foreign, Commonwealth & Development Office (FCDO).
Most of the hacked documents appear to be relatively old, with some dating back as far as the early 2010s and the most recent from January 2022. While some documents are clearly linked to specific publicly known hacks, such as the 2018 hack on the Institute for Statecraft, it is unclear based on publicly available information whether Underside is also using any documents which were not previously known to have been taken.
Underside is operating with the knowledge and repeated public endorsement of the Russian government. It appears to have access to funds, despite having no obvious source of income. It began in December 2021, shortly after a previous social media campaign to publicise what appears to be largely the same corpus of hacked documents appears to have ceased.
The goal of the Underside operation appears to be to build a public case for the targeting and harassment of Russian individuals and organisations who have past or present associations with the UK Government. This is occurring in the context of a renewed major government crackdown on civil society and independent media within Russia, as well as purges of those within the Russian elite who are perceived as being pro-Western or insufficiently enthusiastic about Putin’s war.
The operation reflects the long tail of risk that hacked information can pose. Many of the hacked documents contain information which may have been considered relatively innocuous and non-sensitive at the time it was stolen. In the dramatically changed circumstances of 2022 however, whoever is behind Underside is seeking to use this information to place individuals and organisations firmly in the crosshairs of the Russian government, and declare open season on them in the minds of the Russian public.
Figure 1. Screenshot of Underside[.]today home page, captured 26 July 2022
Key Takeaways
➜ The Underside project illustrates the long tail of risk associated with hack and leak attacks. While much of the information contained in the hacked documents may have been considered relatively innocuous at the time it was taken, in the dramatically changed circumstances of 2022 the same information appears likely to be used to harass or harm innocent individuals and organisations.
➜ The primary audience of the Underside project is domestic, as are the primary targets for doxxing attacks. The targets include journalists, civil society activists, academics and other overt opponents of the Putin regime, but also high-ranking members of the Russian government. These individuals appear to have been singled out for being perceived as being too pro-Western. This is occurring against a broader backdrop of internal purges within the Russian elite of those who are seen as being too close to the West or insufficiently supportive of Putin’s war in Ukraine.
➜ Underside is operating with the public support of high-level Russian government officials. Public endorsements from officials began very early in the campaign. Underside uses documents suspected to have been hacked by Russian state actors, and operates in support of the Russian government’s interests. Although it is difficult to make a firm attribution based on open sources, a reasonable hypothesis based on the evidence is that Underside is directly linked to or run by Russian state actors.
Timeline
Before the February 2022 invasion:
In 2018, hackers posing as the hacking collective Anonymous but suspected to be linked to Russia leaked a trove of documents hacked from the Institute for Statecraft to a website, Cyberguerrilla.org.
In February 2021, after Cyberguerrilla went down, a social media campaign disseminating the same and additional hacked documents began operating, including in English, often using the username ‘Matthew Doer’ or ‘Matthew Doerr’. This took the form of a series of long-form blog posts discussing the individuals and organisations featured in the hacked documents, and links to download copies of the documents themselves.
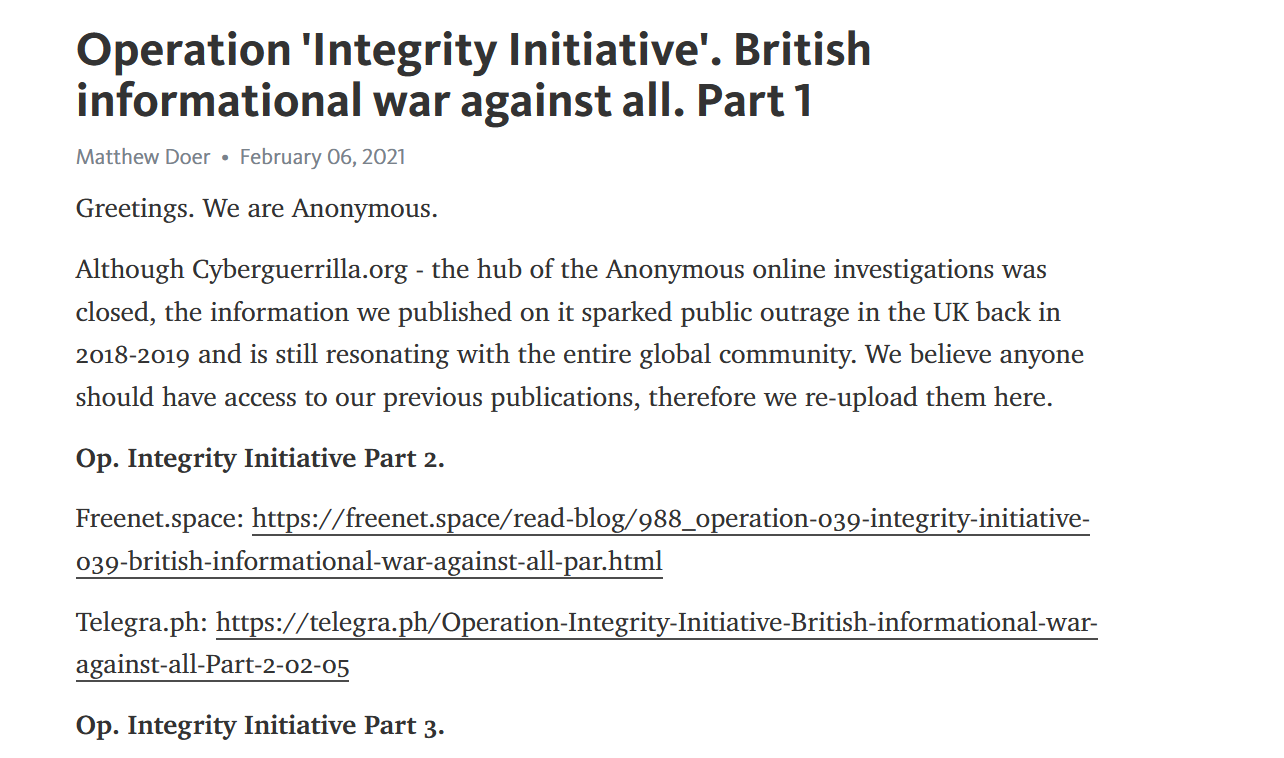
Figure 2. Partial screenshot of Telegra.ph post by ‘Matthew Doer’ sharing links to hacked documents.
On 27 February 2021, the Russian Foreign Ministry’s Twitter account shared a screenshot of a ‘Matthew Doer’ post, alongside a comment from Foreign Minister Zakharova about the hacked documents.
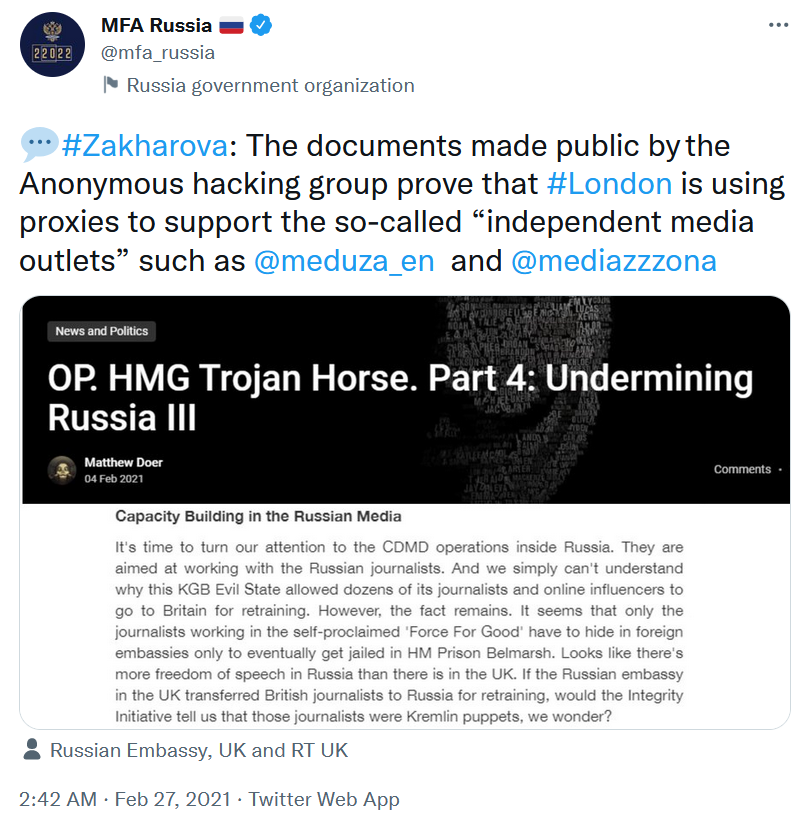
Figure 3. Screenshot of @mfa_russia tweet sharing a screenshot of a ‘Matthew Doer’ post.
This social media campaign was also used to leak new documents hacked from the FCDO and to frame a narrative around them. Some of this content was picked up by fringe Western media outlets, particularly The Grayzone, which published multiple pieces which closely resembled “Matthew Doer’s” posts, and in some cases linked directly to them. At least once, ‘Matthew Doer’ linked back to The Grayzone’s coverage of their content, describing it as “excellent.”
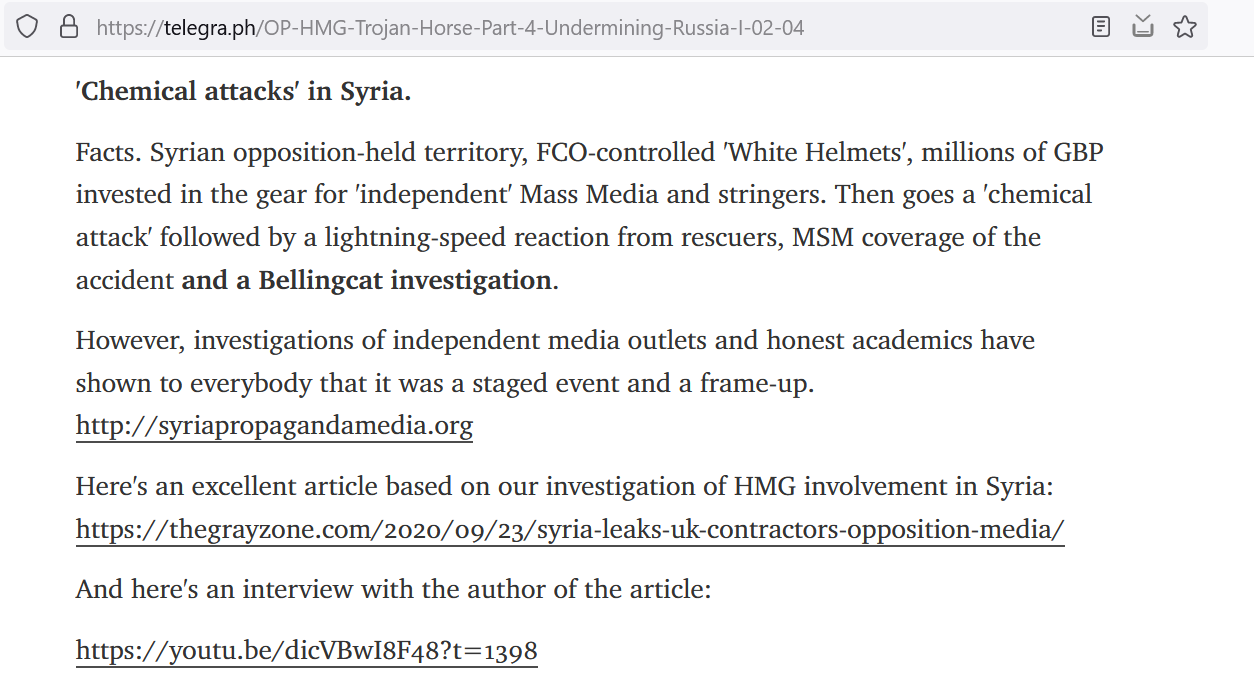
Figure 4. Screenshot of Telegra.ph post by ‘Matthew Doer’, praising The Grayzone.
The documents themselves were uploaded to several free file-sharing sites. It appears that these download links were expiring frequently (this seems to have been largely due to limitations on free usage rather than content moderation by the file-sharing platforms).
On 3 November 2021, the domain britishfiles[.]com was registered in Russia, using clearly fake details and the email address vactinion[@]protonmail[.]com. What appears to be the same set of hacked documents is linked to on the site in English and Russian, using the same headings and other descriptions as the ‘Matthew Doer’ posts. The documents themselves are hosted on Amazon AWS. The site again claimed that the documents had been hacked by the Anonymous hacking collective.
![Screenshot of Britishfiles[.]com.](https://www.isdglobal.org/wp-content/uploads/2022/08/F5-Brittish-files.png)
Figure 5. Screenshot of Britishfiles[.]com.
On 30 November 2021, a British Files Telegram channel was created. It did not become active until March 20th 2022, however, and has posted only three times as of July 2022. The British Files site appears to serve primarily as a repository for hacked material, thus solving the problem that the ‘Matthew Doer’ campaign was having with free upload sites.
The final ‘Matthew Doer’ post (as of July 2022) was published on 8 December, 2021.
On 15 December 2021, the domain underside[.]org was registered by a Russian registrar. The domain used Cloudflare to protect other details about its registration.
From 20 December onwards, the “Underside editors”, as they refer to themselves, began to publish a series of long-form articles combining the files uploaded on Britishfiles.com with open source data to dox primarily Russian individuals and organisations with links to the UK. This included journalists, media organisations, civil society activists, business people, philanthropists and even Russian political figures accused of being too close to the West.
On 3 January 2022, the Russia Foreign Ministry’s Facebook page published an English-language opinion piece by Spokesperson Maria Zakharova, in which she commended the work of Underside and linked directly to the Underside[.]org domain. This post was subsequently shared by other Russian diplomatic accounts including the Russian Embassy in London.
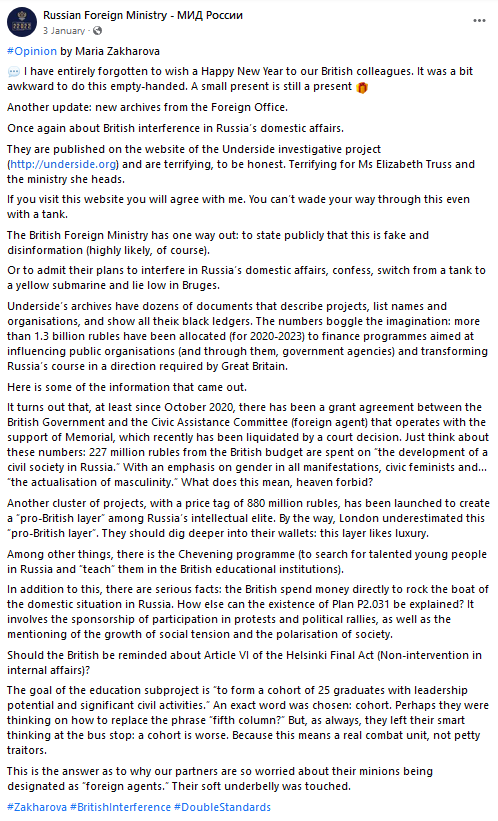
Figure 6. Screenshot of Facebook post by the Russian Foreign Ministry on 3 January 2022.
On 30 January, the Underside Telegram channel was created, and has since been used to tease upcoming articles and to share snippets of newly published pieces.
On 4 February, Zakharova again publicly referenced Underside, and this was tweeted out by the @MFA_Russia Twitter account.
On 24 February, the day Russia launched its full-scale invasion of Ukraine, a new domain underside[.]today was registered.
After the February 2022 invasion:
On 25 February, the Underside Telegram channel posted that they had lost access to their .org domain due to complaints, and shared their new domain underside[.]today.
A vengefully-toned post on 26 February threatened that “All those who work for Britain and act on the instructions of the Foreign Office will be named by name… Hiding is no longer possible. All you can do is repent and start actively sharing information – earn yourself an indulgence before the Russian army takes Kyiv. Submit information to underside_org@protonmail[.]com.” [translated].
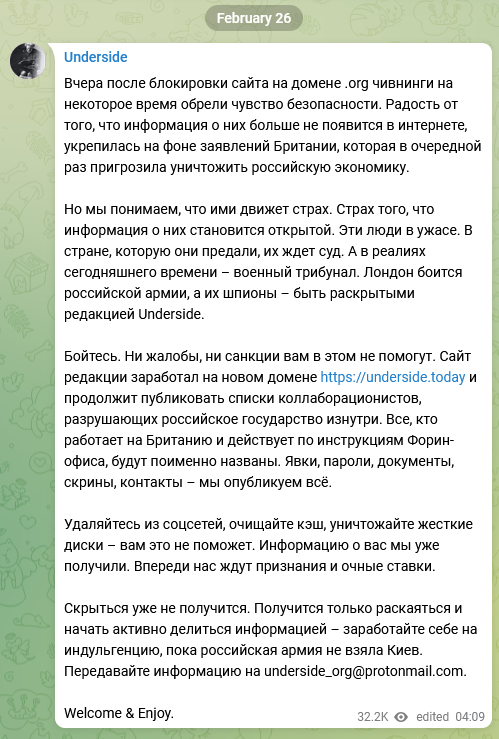
Figure 7. Screenshot of Telegram post from @underside_org.
Underside resumed publishing long-form articles doxxing individuals and organisations with links to the UK. In these articles the writers repeatedly called for the Russian authorities to take up their findings and use them for prosecutions or other forms of retaliation. Underside’s articles have been periodically picked up and reported on by Russian state or state-friendly media.
On 29 March, the spokesperson for the State Duma Commission to Investigate the Interference of Foreign States in Russia’s Internal Affairs said that the Commission would study the investigations published by the “internet resource” Underside[.]today into graduates of the Chevening program . The Chevening program, an international scholarship program funded by the FCDO, has been a major focus of Underside’s doxxing efforts). This occurred at a time when Underside had only a few thousand Telegram followers, suggesting it did not have a high profile among the general public.
On 21 April Zakharova again publicly commended Underside.
On 13 May, Underside published a public call for writers to submit their own investigations (via the email addresses dr_moroooo@protonmail[.]com or underside@tutanota[.]com) based on the documents published by britishfiles[.]com. Notably, Underside offered to pay for these pieces. Pay rates offered were:
➜ 25k RUB for a news article (5000-10000 characters, 3-5 sources). As of 1 August exchange rate, this is roughly 330 GBP.
➜ 60k RUB for a long read (20000+ characters, more than 3 sources). As of 1 August exchange rate, this is roughly 792 GBP.
As of July 2022, Underside has turned a particular focus to the British Council, publishing multiple articles on individuals and organisations linked to the Council and calling for the Russian government to declare it an undesirable organisation.

Figure 8. Screenshot from an underside[.]today article dated 7 July 2022, calling on agencies of the Russian government to declare the British Council an undesirable organisation under Russian law.
On 13 July, for the first time Underside republished a translation of an article from another outlet (all previous posts were of original content). The article, originally published on May 20th in MintPress News, was written by The Grayzone contributor Kit Klarenberg. It focused on Nina Jankovic’s career and the US government’s turbulent and short-lived proposal for a ‘Disinformation Governance Board.’
In the article, Klarenberg made use of documents from the FCDO which appear to have come from the corpus of hacked documents used by ‘Matthew Doer’, British Files and Underside. The Underside translation ended with an invitation to Klarenberg for future cooperation. It is unclear whether Underside has directly reached out to Klarenberg.

Figure 9. Screenshot from Underside translation of Klarenberg’s article on Nina Jankovic, publicly encouraging Klarenberg to contact them via email.
On 26 July, Russian State Duma deputy Andrei Lugovoi (suspected to have been directly involved in the killing of Alexander Litvinenko in Britain. Russian authorities rejected an extradition request for Lugovoi by the British government in 2007) released a documentary on RuTube (a Russian social media platform similar to YouTube) about the Institute for Statecraft, the Integrity Initiative and related topics. He linked directly to the Matthew Doer posts in the description.
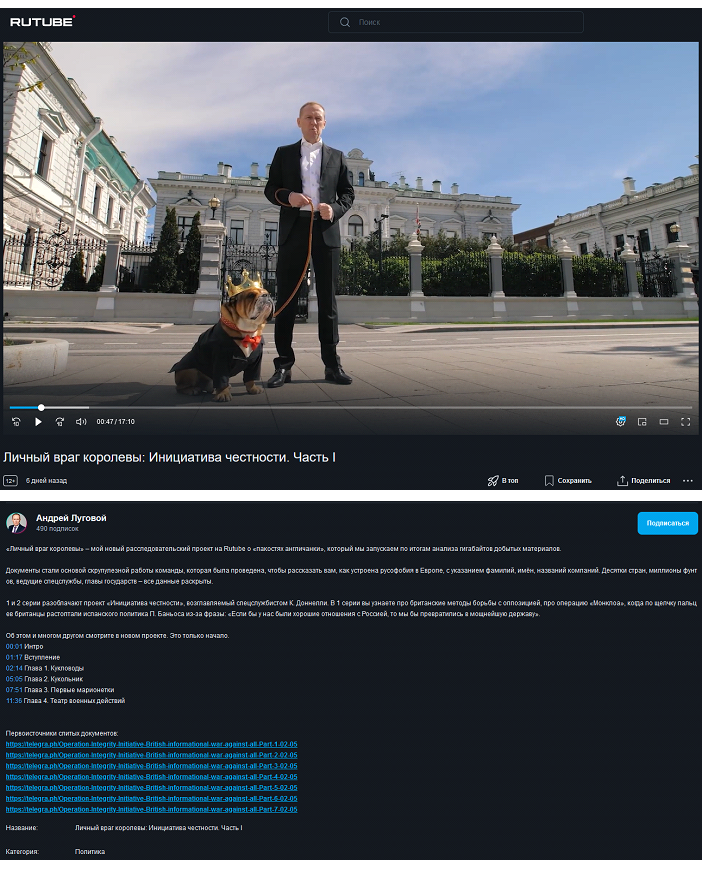
Figure 10. Screenshots of RuTube documentary and description showing links to ‘Matthew Doer’’s Telegraph posts.
As of the time of writing, August 2022, the Underside operation is ongoing with new articles targeting thinktanks and NGOs including the Carnegie Centre in Moscow, Chatham House, the Atlantic Council and others.
Targeting
Underside publishes three types of content:
➜ Long-form ‘investigation’ pieces, which build a narrative around a combination of hacked and open source data.
➜ Organisational profiles, which include a short description of the organisation’s alleged misdeeds against Russia and list the organisation’s website, social media profiles, telephone numbers, addresses etc.
➜ Individual profiles, which list the personal details of individuals including full names, birthdates, addresses, phone numbers, personal social media profiles, work histories etc.
The Underside project expands significantly on the targets and topics covered by the ‘Matthew Doer’ campaign (which focused primarily on hacked documents from the Institute for Statecraft and FCO in relation to the Integrity Initiative and programs in Syria, Lebanon and the Balkans). This difference appears to be that, while the ‘Matthew Doer’ campaign was mainly geared towards exposing alleged British nefariousness and duplicity on the world stage, Underside is first and foremost about rooting out internal enemies of the Russian state.
A partial list of Underside’s main focuses as of early August 2022 includes:
➜ Chevening Scholarship alumni: Graduates from the Chevening Scholarship program have been a major focus of Underside’s articles. Underside has doxxed dozens of recipients (including names, birthdates, email addresses, home addresses, workplaces, personal social media accounts and more) of the scholarship who have gone on to work in positions in the Russian government, state-owned enterprises, civil society, law, media and significant private-sector corporations. Underside portrays Chevening Scholarship alumni as a sinister web of British influence expanding throughout Russian society, painting those individuals as a threat to Russia and therefore putting them at threat in Russia.
➜ The British Council: Through July, the British Council became a focus for Underside’s efforts. They claim that the Council is a front for MI6’s “anti-Russian operation”, which also incorporates the Chevening program, the UK-Russia University Alliance Program, tourism promotion for VisitBritain and even English-language classes. Underside has called for the British Council to be listed as an undesirable organisation under Russian law. If this occurs, it may have serious implications for individuals and organisations in Russia who have worked with the British Council in the past, and could potentially deter others from working with the British Council in the future.
➜ The Open Information Partnership: The FCDO-funded Open Information Partnership and linked organisations Zinc Network and the Expose Network have been the subject of major Underside ‘investigations’. One of Underside’s Telegram posts about the Zinc Network has been viewed over a million times (as of a month after posting). Other posts have doxxed individuals and organisations linked to the OIP. Underside portrays the OIP as a tool of the British government, which is deliberately and maliciously seeking to smear Russia’s reputation and waging information war against Russia via its proxies around the world. Underside also uses the OIP as a way of attacking independent Russian media such as Meduza and Dozhd.
Significance
The clear central purpose of the Underside project is to put Russians with connections to the UK government in danger, and to build a public narrative justifying state harassment, repression or violence against them.
At a minimum, Underside is being utilised by the Russian government to this end. The repeated public support and endorsement of Underside’s work by Zakharova and members of the Russian Duma indicates that the Russian government recognises and values the role which Underside could play in creating a form of online show trial for troublesome individuals and organisations.
A reasonable hypothesis based on the facts is that Underside is itself being run by some part of the Russian government or security apparatus. It uses documents believed to be hacked by Russian state actors; it supports Russian state narratives; it has a budget despite having no apparent source of income; and it has received public support and amplification from some of the highest levels of the Russian government, dating back to early in the operation when its footprint was very small. It is, however, difficult to confirm this hypothesis based on open sources.
There does, however, appear to be some evidence of payments occurring. A close inspection of the underside[.]today website found what appears to be an Ethereum wallet coded into the site. There is no obvious interface on the site itself for the wallet. As of September 12th 2022, the wallet had transacted eight times. A total of 15.05 ETH (over $26,300 US at the September 12th exchange rate) had been deposited in two transactions in June and July from what appears to be a crypto exchange or tumbler wallet. Six outgoing transactions had been made, including three to the same destination wallet, adding up to a total of 3.6 ETH ($6306 US). The size of these transactions suggests that they may be payments of the kind which Underside has been offering to writers. As of September 12th, 11.44 ETH ($20,025 US) remains in the wallet.
The Underside project should be understood in the context of both a domestic and an international information war.
Domestically, it feeds into the Putin regime’s push for greater internal repression and purges of pro-Western Russians at all levels of society. It helps to create a public justification for crackdowns on civil society, independent media and pro-Western political voices. At the same time, it serves as a warning to the Russian population: cooperating with the West, and particularly the UK, is dangerous, and anyone who does so should not think that their secrets are safe.
While it is primarily directed at a domestic Russian audience, Underside is also a part of the international information war. It is a continuation of the years-long hack and leak campaign targeting the FCDO and aligned organisations such as the Institute for Statecraft, in the context of the wider geopolitical struggle for influence between Russia and the West.
For example, if Russian journalists, civil society activists, business figures, and even ordinary people who simply accepted a British scholarship are publicly seen to be subject to harassment and repression as a result of their links to the FCDO, this may have an impact on the willingness of individuals and organisations in other countries to engage with the FCDO, particularly where those countries have their own repressive governments.
Painting the activities of the FCDO, OIP and related efforts as part of a broader malign plot to spread disinformation about Russia also serves a propaganda purpose. A key goal of Russia’s strategy in the information space is to spread an all-pervasive sense of doubt and distrust. In other words, to some extent, it doesn’t matter whether audiences believe the Russian version of events or not, so long as they don’t believe or trust Western information sources either.
The Underside project highlights the long tail of risk from hack and leak campaigns. At the time in which most of the documents appear to have been hacked, the information they contained may have seemed relatively innocuous. In the dramatically changed circumstances of 2022, however, it seems possible that this information may contribute to organisations being banned in Russia, and perhaps individuals being arrested or persecuted.