Project Nemesis, Doxxing and the New Frontier of Informational Warfare
23 June 2022
By Elise Thomas
In late May 2022, an organised campaign to dox (a practice of maliciously publishing personal information online) members of the Ukrainian military, secret services, volunteers and international trainers assisting Ukraine in its fight against Russia’s invasion began to spread across social media. The operators of this campaign claim to be a group of patriotic Russian hackers engaging in a volunteer effort they have dubbed Project Nemesis.
_________________________________________________________________________________
Project Nemesis includes a website publishing the photographs and personal details of hundreds of individuals fighting on behalf of Ukraine, including birth dates, addresses, telephone numbers, passport numbers, personal social media profiles and more. It also incorporates a Telegram channel which posts multiple times a day, highlighting particular individuals who have been doxxed on the site and encouraging their thousands of followers to mock or harass them. As of early June 2022, there are also indications of an effective media strategy to amplify Project Nemesis and further its goals.
The individuals doxxed on the website include alleged members of the Ukrainian military, in particular members of the Azov Battalion and Pravyi Sektor, two groups which have been singled out for their connections to the far-right. Russian propaganda has relied heavily on distorting the real but nuanced problem of links between the Ukrainian military and far-right and neo-Nazi groups.
Project Nemesis also claims to have hacked and published the details of 700 members of Ukraine’s Security Service, the SBU. ISD has not verified this data. Russian state media has reported that a member of the Russian security services believes it is authentic.
It is unclear exactly who is behind Project Nemesis and what, if any, connection it may have to the Russian state or security services. What is clear, however, is that this is a new and aggressively personal salvo in the information war which shadows the conflict on the ground.
Overview
The use of mass doxxing as a psychological and information weapon is a growing feature of modern political conflicts. Over the past two decades, online doxxing has emerged as a significant typology of technology-facilitated violence directed at individuals. This may take place in the context of abusive interpersonal relationships, but many doxxing attacks also have a political component, for example the doxxing of journalists, political activists, government officials and even law enforcement officers.
Mass doxxing as a weapon in a military conflict has several clear benefits for the doxxers. It allows for personalised attacks at scale, creating emotional and psychological stress for individual soldiers and for their families. It may create tensions and demoralisation within the opposing organisation’s ranks if doxxed soldiers feel that their personal information was not adequately protected. It is valuable propaganda which doxxers can use to mobilise and whip up their supporters, and it offers the potential to essentially crowdsource harassment by enabling and encouraging enraged supporters to contact and abuse the targets and their families. When leaked to the media or published through an anonymous or pseudonymous website, the doxxers can also maintain a level of deniability.
There have been several examples of such mass doxxing efforts in recent military and civil conflicts. During the Hong Kong protests in 2019, for example, an anonymous website appeared which published the personal details of protesters and their supporters, as well as journalists. The site included photographs of individuals overlaid with crosshairs.
In Ukraine, the role of the pro-Ukrainian ‘Peacemaker’ website in doxxing alleged Russian supporters and collaborators since 2014 has been highly controversial. The volunteer-run site was founded by a member of Ukraine’s interior ministry and is alleged to have close ties to the Ukrainian security services. At least two people were murdered days after their personal details and home addresses were published on the site.
In 2017, the UN High Commissioner for Human Rights called for Ukrainian authorities to launch an investigation into the site and force it to remove personal details. As of June 2022, the Peacemaker site continues to operate and continues to publish personal information.
In another example of weaponised doxxing, in April 2022 the hacker collective Anonymous claimed to have hacked the personal data of 120,000 Russian soldiers and published it on the leaks website DDoS Secrets.
Project Nemesis, which in some ways appears to be a pro-Russian equivalent of Peacemaker, appears to have been in the works since at least mid-March 2022. The website has been constructed and populated with data over a period of several months. In late May 2022, the operators launched a Russian-language Telegram channel and began publicly promoting the website and encouraging Telegram users and others to actively engage with the data.
In the introductory post in their Telegram channel, the operators position themselves as “IT volunteers and OSINTers” aiming to hunt down and expose Ukrainian Nazis and “those who help them”. Elsewhere they identify themselves as RaHDit, a group of Russian patriotic hackers which has been claiming credit for multiple attacks on Ukraine since February.
The Project Nemesis Telegram channel has achieved a rapid and largely organic growth in followers, gaining roughly 30,000 subscribers in its first week and over 50,000 by the end of the second week. This growth is likely due to the way it has been actively and repeatedly promoted by multiple large Russian propaganda channels and featured by Russian state media online and on television.
What is the purpose of Project Nemesis?
The clear purpose of Project Nemesis is intimidation. In the context of the conflict on the ground, doxxing may have immediate implications for morale and operational security in combat. Doxxing ordinary soldiers and other individuals linked to the war effort can also expose them and their loved ones to harassment and other potential harms, both now and in the future. In 2019, for example, it was reported that the partners of Dutch fighter pilots participating in patrols of Baltic air space were receiving harassing phone calls from “people with a Russian accent”.
The operation has had a particular focus on doxxing allegedly LGBTQI+ Ukrainians. Doxxing based on their sexuality creates an additional dimension of harm and potentially exposes those individuals to homophobia or discrimination. The US representative to the United Nations has warned that the US believes Russian forces may deliberately target LGBTQI+ populations. LGBTQI+ individuals and communities have faced intense persecution and human rights violations in the occupied areas of eastern Ukraine since 2014.
Homophobic doxxing is also a long-running problem in the rest of Ukraine. Ukrainian far right Telegram channels regularly publish the personal details and photographs of LGBTQI+ activists, along with feminist and left-wing activists. This doxxing has contributed to threats and harassment against some LGBTQI+ individuals in government-controlled Ukraine in the past.
Doxxing the employees of an intelligence service adds another layer. It is a demonstration of capability, a way of signalling – to Ukrainians, to the world, and perhaps most significantly to domestic audiences in Russia – that the Ukrainian SBU is unable to keep their own systems safe from Russian hackers.
Who are the hackers?
The operators of Project Nemesis, who go by the name RaHDit, describe themselves as a “group of IT volunteers and OSINTers” who are using their hacking skills to support Russia’s war in Ukraine out of a sense of outrage against Nazis in Ukraine.
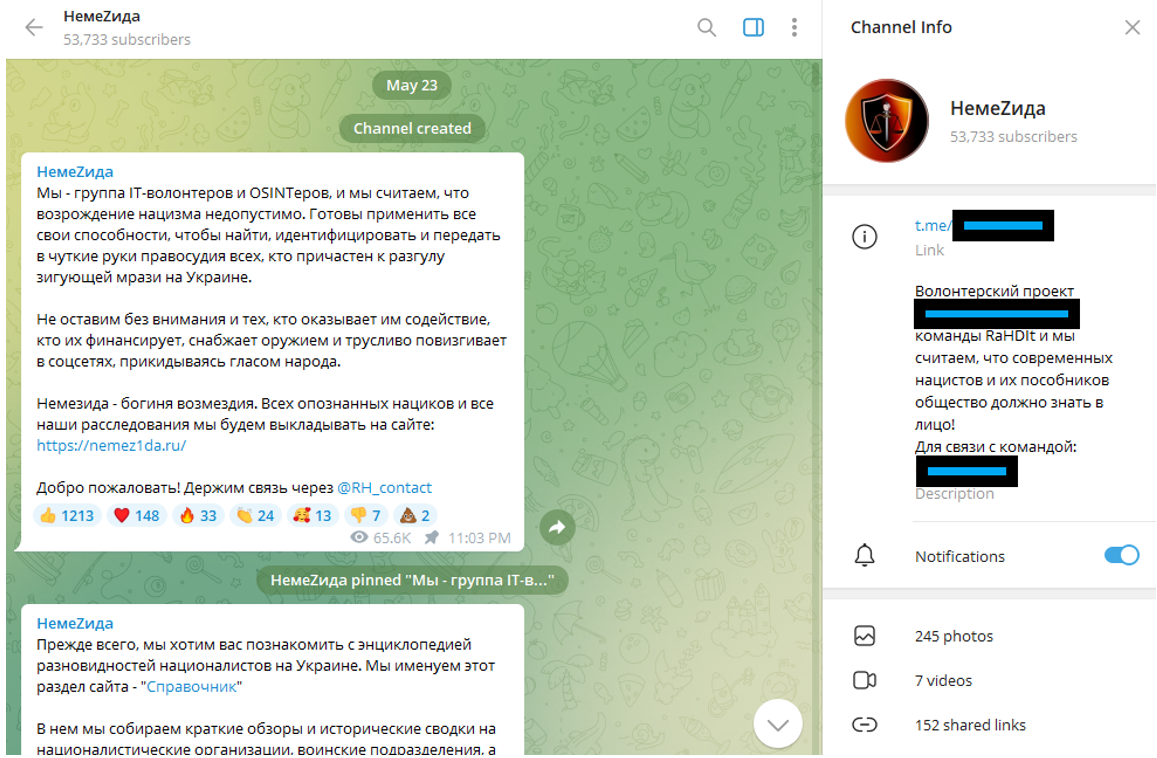
Image 1: Screenshot of first post and Channel Info for the Project Nemesis Telegram channel.
Based on searches of social media and a report from the Mandiant cybersecurity firm, RaHDit was not a known hacker group prior to Russia’s invasion of Ukraine in February 2022. The name seems to have first surfaced in the early weeks of the war, when reporting in the Russian media gave credit to RaHDit for hacking Ukrainian government and news media websites. This included allegedly taking down 755 ‘.gov.ua’ domains.
On 3 March, pro-Kremlin outlet Lenta.ru wrote that “a source in the information security field” had alerted them to a Russian hacker group called RaHDit, which had hacked the sites and posted a message to Ukrainians (Lenta noted they were not able to verify these claims). Screenshots of the alleged RaHDit hack were also shared on Telegram in pro-Russian channels.
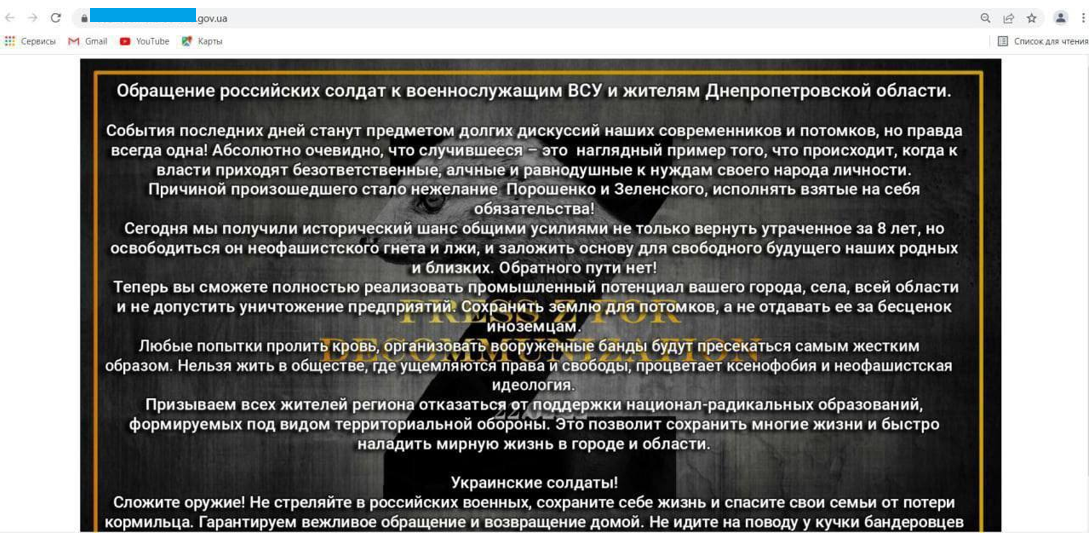
Image 2: Screenshot of alleged RaHDit hack and defacement attack on Ukrainian government site, shared in pro-Russian Telegram channels.
RaHDit is one of several self-professed Russian patriotic hacker groups which have materialised following Russia’s expanded invasion of Ukraine in February 2022. Other groups include KillNet and XakNet . RaHDit, KillNet, XakNet and potentially others appear to have sprung up, at least partially, as Russia’s answer to Anonymous and other pro-Ukrainian hacktivist groups. There is some level of collaboration between RaHDit and Beregini, a pro-Russian hacker group which has been active since 2016 and adopts the personae of a group of Ukrainian women.
There is also some degree of mutual support between RaHDit and KillNet. KillNet has promoted Project Nemesis on their own channel, and RaHDit has posted in the Project Nemesis channel to encourage their followers to follow KillNet’s new channel.
In early March, posts and a video on Telegram claimed that KillNet had hacked the SBU and stolen data on employees. This data, if it ever existed, does not appear to have been published. It is unclear whether there is a connection between this data and the data published by RaHDit.
The American cybersecurity firm Mandiant notes that the “degrees of affiliation [of these groups] to the Russian state are yet unknown”. One significant aspect of the hacking and cybersecurity community in Russia is that there is frequently a grey zone between non-state and even criminal hacking groups , and the intelligence services. This makes it difficult to establish clear attribution even when activity is clearly emanating from Russian actors.
The Operation
The Site
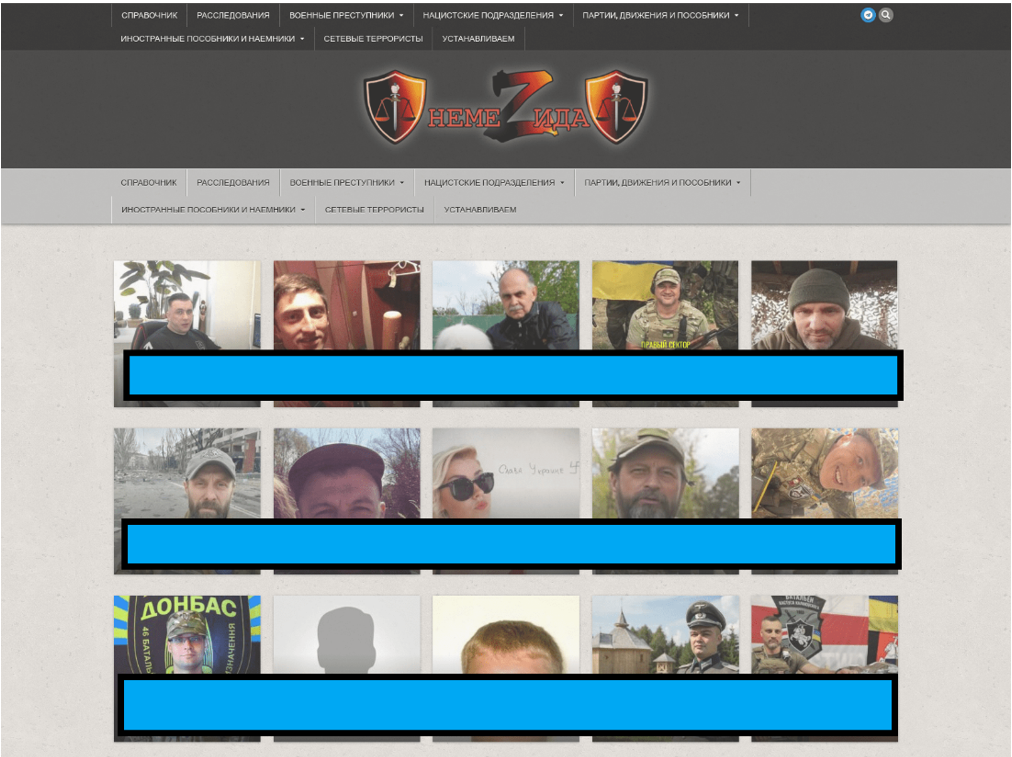
Image 3: Screenshot of Project Nemesis homepage with names and details obscured by ISD, captured 8 June 2022.
The cornerstone of Project Nemesis is the website, which publishes what it claims to be the personal information of hundreds of members of the Ukrainian military and security services, as well as international military trainers assisting Ukraine in its fight against the Russian invaders.
The website lists the profiles of individuals under several categories. These categories include ‘War Criminals’, ‘Nazi Units’ and ‘Network Terrorists’. The information published about each individual varies significantly. Some information appears likely to be taken from internal records; in other cases, it appears to have come from open sources such as social media profiles.
The most significant element of the site to date is that it claims to publish the details of 700 members of the Ukrainian Security Service or SBU. In a Telegram post announcing the publication of the SBU employees’ details, the Project Nemesis operators implied that they had hacked the computer of an SBU employee and stolen the data. ISD has not verified whether this data is authentic.
The website does not provide information about who is running it. The domain nemez1da[.]ru was registered on 13 March 2022, using an IP address in Irkutsk, Russia. It uses Whois privacy protections to conceal the registration details for the domain, and protection from distributed denial of service (DDoS) attacks from Russian service provider DDoS-Guard. Based on the upload dates of images to the website, the content appears to have been steadily uploaded over a period of more than two months, from March 2022 until the public launch of the site in late May 2022.
The PTR record for the domain points to another domain with a .ru suffix. The DNS SOA email associated appears to belong to the same individual.
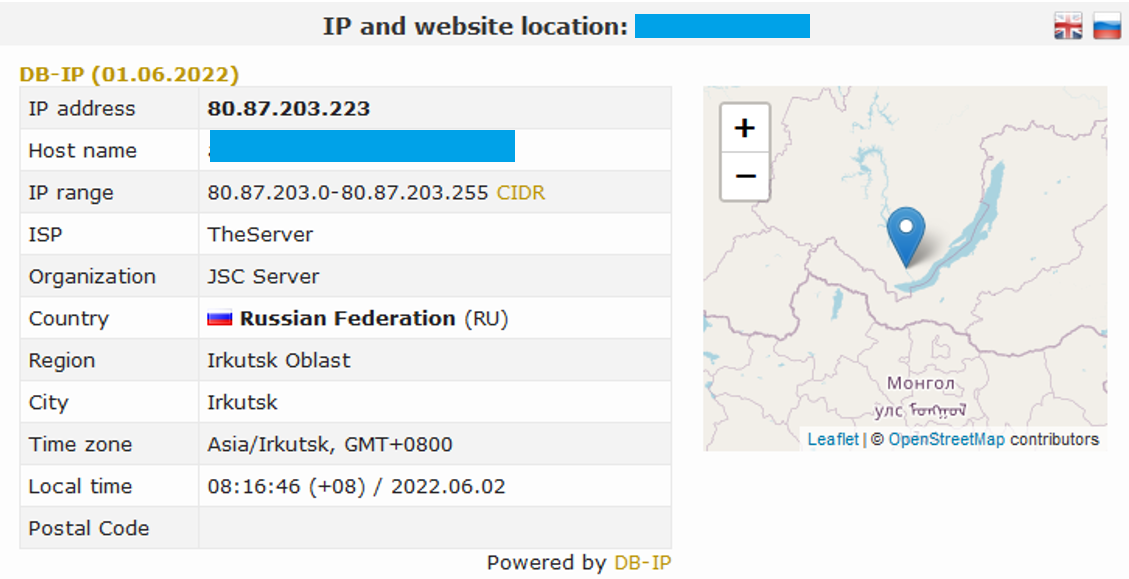
Image 4: Screenshot of details for the domain.
Searches have found accounts using the same handle, aleksandr.muhin.muhin, on a small number of websites including a fitness tracking platform, a mountain biking forum and an English language learning platform for Russian speakers. Although the handle is distinctive (there are many Aleksandr Muhins, but very few uses of the double surname), this is circumstantial, and it is not confirmed whether there is a link between these accounts and the site creator(s).
Unusually, the website creators also appear to have created dozens of subdomains which redirect to the homepage. These subdomains have been included in the main domain’s catch-all SSL certificate. Many contain a seemingly random combination of domains for other unrelated sites, or usernames for various forums and social media sites. There appears to be no common theme or obvious connection, and it is unclear why they have done this.

Image 5: Screenshot of SSL lookup for the domain, captured 2 June 2022.
The Telegram Channel
While the website is the core of Project Nemesis, its social media presence appears to be a key part of the strategy for driving engagement and funnelling users towards the site.
The Project Nemesis Telegram channel was created on 23 May, and had almost 50,000 subscribers as of 6 June. The channel operators post multiple times a day, highlighting specific individuals who have been doxxed on the site. There is no clearly discernible pattern to the posting schedule in the first two weeks of the channel’s existence.
The channel allows and encourages comments, and the posts are clearly intended to evoke feelings of outrage in Russian followers. In the example below, the channel has posted a picture of a man appearing to urinate on a Soviet flag. The post text asks, “Don’t you think that this pissing boy [name redacted] from the Azov Regiment is begging for us to remember this act?”
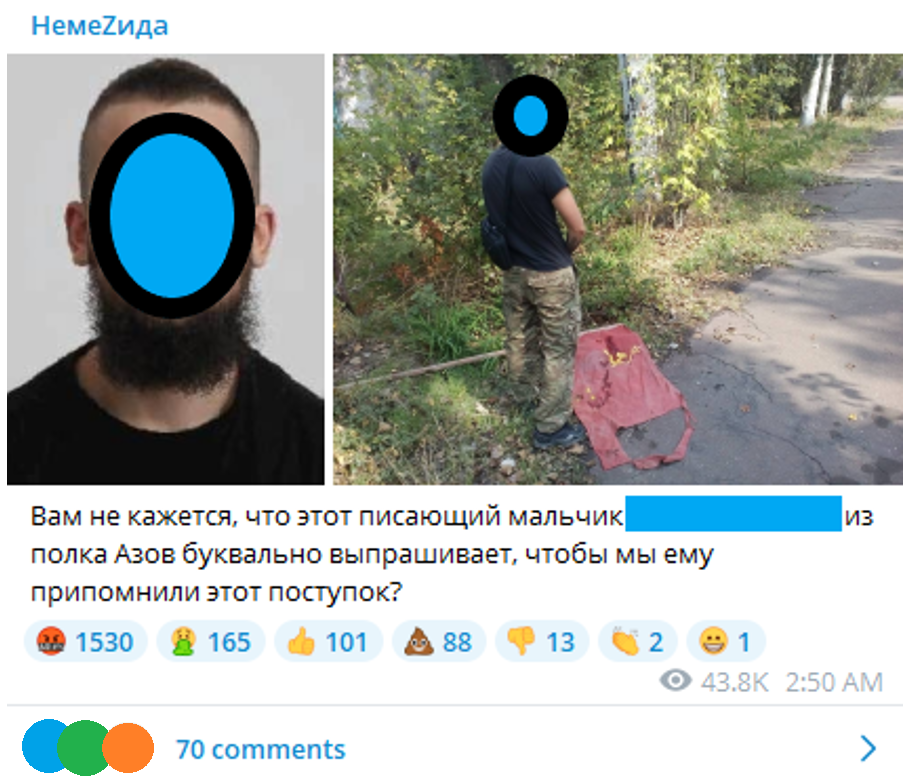
Image 6: Screenshot of post in @nemez1da_ru Telegram channel, posted 26 May 2022, captured 2 June 2022.
The posts highlighting specific individuals as targets for outrage have two broad focuses: alleged Nazis and far-right supporters, and allegedly LGBTQI+ individuals. The tone of the posts treats these alleged traits as more or less equally wicked, and deliberately stokes homophobic and violent commentary from the channel’s followers. This is a clear homage to the homophobic rhetoric and actions of the Putin regime both in Russia itself and specifically in relation to the war in Ukraine.
Below, for example, is a post doxxing an allegedly gay SBU employee. The post links to a detailed “investigation” of his alleged use of gay dating and kink websites.

Image 7: Screenshot of post in @nemez1da_ru Telegram channel, posted 1 June 2022, captured 7 June 2022.
The Telegram channel is also used to solicit the active participation of members of the public. Followers are encouraged to send in their own information and tips for possible inclusion on the website. The channel has encouraged followers to use the information published on their site for harassment.
On 2 June, the day after Project Nemesis published the alleged SBU employee data, the channel posted a poll asking followers whether they had used the phone numbers published to call and harass the SBU employees. Only 3% (of 7061 respondents) said they had. Over 50,300 people saw the post, according to Telegram’s metrics. The fact that they posted the poll indicates that the goal of the operation is not limited to publishing the material for their followers – they also want their followers to use it to harass their doxxing victims and are interested in collecting data on how many of their followers are doing so.
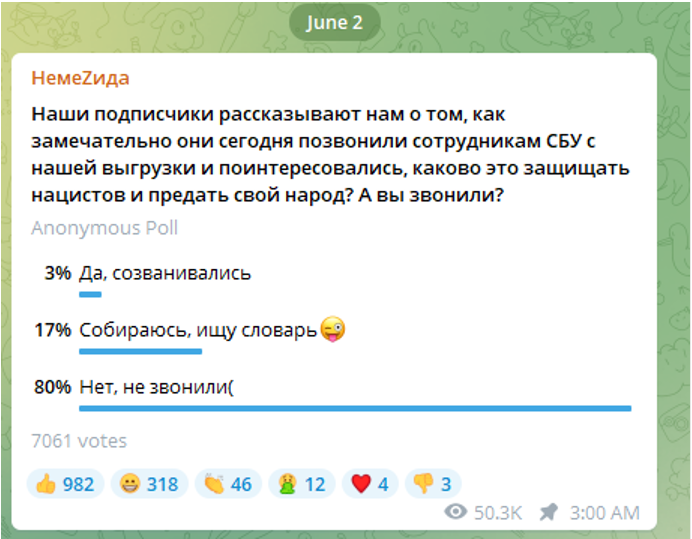
Image 8: Screenshot of post in @nemez1da_ru Telegram channel, posted 2 June 2022, captured 7 June 2022.
The Project Nemesis Telegram channel’s follower growth appears to have been largely organic. In the first week of its existence the channel was repeatedly mentioned and shared by several large pro-Kremlin propaganda Telegram channels, driving thousands of subscribers to the channel. On 26 May, for example, the Project Nemesis channel received 54 mentions from other channels and gained over 10,000 new subscribers in a single day.
The biggest boost to date, however, followed the appearance of a member of RaHDit on the Russian state media outlets Ria Novosti and Izvestiya. After these interviews, which will be discussed further below, the channel gained 15,093 new subscribers in a day on 2 June.
The Media Strategy
In a media appearance on 2 June, which coincided with, and was likely timed with, the publication of the SBU data the previous day, a member of RaHDit gave a filmed interview (showing the back of his head and using a voice modulator) to Russian state media outlet Ria Novosti.
In the interview, the speaker claimed that RaHDit had hacked evidence and had been given other hacked documents by the Beregini group. The speaker claimed that this evidence proved that Ukraine had been planning an attack on the Russian Federation and the occupied territories of the Donbass and Crimea. The speaker then suggested that due to this, Russia’s “special military operation” in Ukraine was justified as a pre-emptive defensive strike. He also claimed to have evidence that Ukraine had been waging psychological operations targeting Russia for years. Ria Novosti also reported that a source in the Russian security services had verified the hacked SBU data published by Project Nemesis as authentic.
In another interview with Russian outlet Izvestiya, also published on 2 June, a member of RaHDit (who may well have been the same individual) was again filmed from behind and with a voice modulator. This interview focused more on Project Nemesis and the hacked SBU employee data. In the interview the speaker alleged that some SBU employees had been hired despite past law-breaking, drug addictions or gambling problems.
The media strategy pursued by RaHDit appears to have been quite effective in spreading the news of the hacked SBU data. Both interviews have been subsequently picked up and republished or repackaged by a wide range of Russian-language and some international media outlets. This has allowed the news of the hacked SBU data to reach a far wider audience than the Project Nemesis website could have achieved alone.
On 8 June, the RaHDit hacker was again featured in Russian state media (although this coverage appears based on the previous interviews) explaining why fractures are supposedly emerging between Zelensky and the Ukrainian armed forces.
The Bigger Picture
Regardless of exactly who is behind Project Nemesis, it serves the interests of the Russian state on multiple levels.
Firstly, and most obviously, it seeks to reinforce the Russian government’s propaganda narrative about rampant Nazism in Ukraine, especially amongst the Ukrainian military. It plays on Kremlin talking points which amplify homophobia for political gain. RaHDit’s appearances in Russian state media have also reinforced the Russian government’s narratives. This includes alleging to have proof that the Russian invasion of Ukraine was justified on the basis that Ukraine was planning a pre-emptive strike on the occupied territories of Crimea and the Donbass.
Secondly, it presents a demonstration of Russian capability and an embarrassment to the Ukrainian security services and military. Whether or not the allegedly hacked SBU data is authentic, the perception that the SBU was easily compromised, and its employees exposed by Russian hackers, may be damaging to the SBU’s reputation and to Ukrainian morale. It may also provide an ego boost for Russia’s supporters.
Thirdly, it offers a Russian riposte to the use of weaponised doxxing by the Ukrainians and their supporters. After the challenges and humiliations presented by Ukraine’s Peacemaker volunteers and the Anonymous hackers, it seems likely that Russian military authorities would welcome an aggressive response from the Russian side.
This is a relatively new and still evolving operation. Much remains unclear about who is responsible for it, their level of resources and the source of their information. What does seem evident is that this kind of hack and leak operation, combined with personal data and weaponised against individuals, is likely to play a greater role in cyber and information warfare going forward.
Elise Thomas is an OSINT Analyst at ISD. She has previously worked for the Australian Strategic Policy Institute, and has written for Foreign Policy, The Daily Beast, Wired and others.